RtlCreateUserThread函数当然也是ntdll导出的函数,这个比之前的NtCreateThreadEx是要强点的,最起码还能看得见参数有几个,hhhhh,难顶啊。
其实CreateRemote和Nt系列和Rtl系列的注入方式和思路基本是一致的,但是这里还是按照惯例,bb一下我的实现思路(这思路我愿意称之为套娃):
- 从控制台得到想要实施注入的目标进程名字
- 得到当前进程所在的目录(GetCurrentDirectory),并保存
- 得到当前进程的位数 (IsWow64Process)
- 根据进程名字得到当前进程的Id
- 根据进程Id得到当前进程的完整路径
- 通过进程完整路径对PE文件解析得到目标进程位数
- 目标与当前进程的位数进行匹配,决定加载哪一个dll(x86 or x64)
- 根据当前进程目录,得到dll完整路径
- 通过GetModuleHandle得ntdll和kernel32模块得句柄
- 通过GetProcAddress分别从ntdll和kernel32中得到RtlCreateUserThread和LoadLibraryA
- 通过目标进程Id,打开目标进程,获得进程句柄
- 在目标进程中申请内存
- 在申请好的内存中写入Dll完整路径
- 利用RtlCreateUserThread启动远程线程执行加载Dll,完成注入
重要部分源码(Win 7 Win10测试):
#include"RtlCreateUserThread.h"
#include"Helper.h"
#ifdef UNICODE
LPFN_LOADLIBRARYW __LoadLibrary = NULL;
#else
LPFN_LOADLIBRARYA __LoadLibrary = NULL;
#endif
LPFN_RTLCREATEUSERTHREAD __RtlCreateUserThread = NULL;
int _tmain()
{
setlocale(LC_ALL, "Chinese-simplified");
TCHAR ProcessImageName[MAX_PATH] = { 0 };
TCHAR CurrentFullPath[MAX_PATH] = { 0 };
TCHAR TargetProcessFullPath[MAX_PATH] = { 0 };
ULONG_PTR TargetProcessPathLength = MAX_PATH;
ULONG ProcessId = 0;
HANDLE ProcessHandle = INVALID_HANDLE_VALUE;
LPVOID VirtualAddress = NULL;
SIZE_T ReturnLength = 0;
BOOL IsOk = FALSE;
BOOL SourceIsWow64 = FALSE;
BOOL TargetIsWow64 = FALSE;
_tprintf(_T("输入一个进程ImageName\r\n"));
TCHAR RcceiveChar = _gettchar();
int i = 0;
while (RcceiveChar != '\n')
{
ProcessImageName[i++] = RcceiveChar;
RcceiveChar = _gettchar();
}
GetCurrentDirectory(MAX_PATH, CurrentFullPath);
IsWow64Process(GetCurrentProcess(), &SourceIsWow64);
ProcessId = KtGetProcessIdentify(ProcessImageName);
if (ProcessId == 0)
{
return 0;
}
IsOk = KtGetProcessFullPath(TargetProcessFullPath,
&TargetProcessPathLength, ProcessId, FALSE);
if (IsOk == FALSE)
{
return 0;
}
KtIsWow64Process(TargetProcessFullPath, &TargetIsWow64);
if (SourceIsWow64 == TRUE && TargetIsWow64 == TRUE)
{
_tcscat_s(CurrentFullPath, _T("\\Dll.dll"));
}
else if (SourceIsWow64 == FALSE && TargetIsWow64 == FALSE)
{
_tcscat_s(CurrentFullPath, _T("\\Dll.dll"));
}
HMODULE NtdllModuleBase = NULL;
HMODULE Kernel32ModuleBase = NULL;
NtdllModuleBase = GetModuleHandle(_T("NTDLL.DLL"));
Kernel32ModuleBase = GetModuleHandle(_T("KERNEL32.DLL"));
if (NtdllModuleBase == NULL || Kernel32ModuleBase == NULL)
{
KtCloseHandle(ProcessHandle);
return 0;
}
__RtlCreateUserThread = (LPFN_RTLCREATEUSERTHREAD)GetProcAddress(NtdllModuleBase,
"RtlCreateUserThread");
if (__RtlCreateUserThread == NULL)
{
return 0;
}
#ifdef UNICODE
__LoadLibrary = (LPFN_LOADLIBRARYW)GetProcAddress(Kernel32ModuleBase, "LoadLibraryW");
#else
__LoadLibrary = (LPFN_LOADLIBRARYA)GetProcAddress(Kernel32ModuleBase, "LoadLibraryA");
#endif
if (__LoadLibrary == NULL) {
KtCloseHandle(ProcessHandle);
return 0;
}
ProcessHandle = KtOpenProcess(PROCESS_ALL_ACCESS, FALSE, ProcessId);
ULONG BufferLength = 0;
BufferLength = (_tcslen(CurrentFullPath) + 1) * sizeof(TCHAR);
VirtualAddress = VirtualAllocEx(ProcessHandle, NULL, BufferLength, MEM_COMMIT, PAGE_READWRITE);
if (VirtualAddress == NULL)
{
KtCloseHandle(ProcessHandle);
return 0;
}
if (KtProcessMemoryWriteSafe(ProcessHandle, VirtualAddress, CurrentFullPath, BufferLength, &ReturnLength) == FALSE)
{
KtCloseHandle(ProcessHandle);
return 0;
}
HANDLE ThreadHandle = INVALID_HANDLE_VALUE;
CLIENT_ID ClientId;
NTSTATUS Status = __RtlCreateUserThread(
ProcessHandle,
NULL,
0,
0,
0,
0,
(PTHREAD_START_ROUTINE)__LoadLibrary,
VirtualAddress,
&ThreadHandle,
&ClientId);
if (Status >= 0)
{
WaitForSingleObject(ThreadHandle, INFINITE);
VirtualFreeEx(ProcessHandle, VirtualAddress, BufferLength, MEM_RELEASE);
KtCloseHandle(ProcessHandle);
}
else
{
VirtualFreeEx(ProcessHandle, VirtualAddress, BufferLength, MEM_RELEASE);
KtCloseHandle(ProcessHandle);
return 0;
}
return 0;
}
#include "stdafx.h"
#include <tchar.h>
BOOL APIENTRY DllMain(HMODULE hModule,
DWORD ul_reason_for_call,
LPVOID lpReserved
)
{
switch (ul_reason_for_call)
{
case DLL_PROCESS_ATTACH:
{
MessageBox(NULL, _T("RtlCreateUserThread"), _T("RtlCreateUserThread"), NULL);
}
case DLL_THREAD_ATTACH:
case DLL_THREAD_DETACH:
case DLL_PROCESS_DETACH:
break;
}
return TRUE;
}
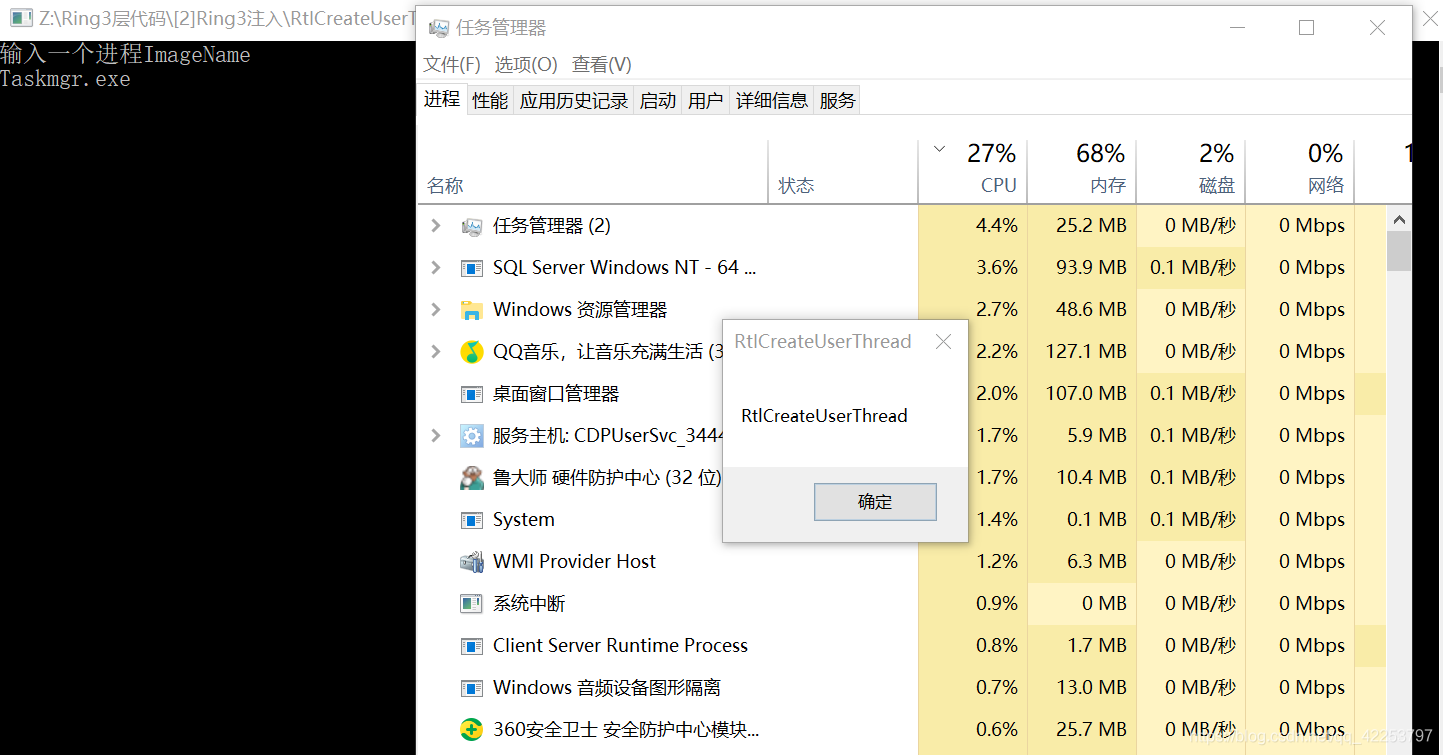
测试通过Win7 x86(Explorer.exe)和Win10 x64(Taskmgr.exe)
今日自勉:永远不要停下自己前进的脚步。
cs





